Vulnerability Management Services
Reduces your vulnerability to attacks
with powerful monitoring and detection services
that keep you both safe and compliant.
Maintaining your IT infrastructure’s security
and its compliance requirements demands continuous
vulnerability scanning, plus knowing the right solutions.
HIFENCE Vulnerability Management supplies both.
You currently don’t have an overview of your IT assets or security posture? You’re not alone. But you are vulnerable, because someone else might find your vulnerabilities first. That’s why HIFENCE provides the accurate, powerful vulnerability monitoring and detection services you need to keep your IT infrastructure safe and in compliance. This includes recommendations for configuration hardening, robust patch management, plus solutions to other external — and internal — attacks.










Key Features:
-
Custom-Tailored to Your Unique Business
Your vulnerability program starts after the HIFENCE Architects Team first matches your security objectives and
roadmaps with your business objectives, all to transform cybersecurity into an invaluable business enabler. -
Comprehensive Vulnerability Test Delivers Realistic Findings
We test your networks, servers, applications and APIs for security vulnerabilities and make realistic recommendations on how to fix them.
-
Know Your Exposure to Threats
We put a magnifying glass on your Internet-facing or internal
applications, services and network so you can get valuable insights on your current cyber security risks. -
Meet Your Compliance Requirements
All of the most important standards are addressed, including PCI-DSS, ISO 27001, HIPAA, SOX, and others.
-
Prioritize Your Security Budget
As an added benefit, the vulnerability report will help you prioritize your security budget and show you where the next investments should be made.
-
Avoid Financial Loss
The damages a single breach of your systems can cause easily reach into the millions of dollars. But our vulnerability program can help protect your organization from such breaches and the catastrophic damages they can cause.
A 360-degree View of Network Vulnerabilities to Strengthen IT, Security and Compliance Posture
Here’s a stunning fact: A single cybersecurity breach can cost your company millions of dollars, while also placing an incalculable toll on your company’s reputation and customer trust in your brand.
Fortunately, HIFENCE Vulnerability Management services can mitigate these dangers by substantially enhancing your security posture, and your company’s future success. Our vulnerability monitoring and detection will provide the most comprehensive, current and accurate picture of your infrastructure. When we detect a vulnerability, we’ll advise you on how to address it — whether it’s a misconfiguration, maintenance of your compliance obligations, or myriad other potential weaknesses. HIFENCE Vulnerability Management services can keep your infrastructure safe and secure from a potentially catastrophic cybersecurity breach. And that’s a fact.
HIFENCE Vulnerability Assessment Process
01. Discover
Identifies all assets
within your environment
05. Test remediations
Confirms that
vulnerabilities are fixed
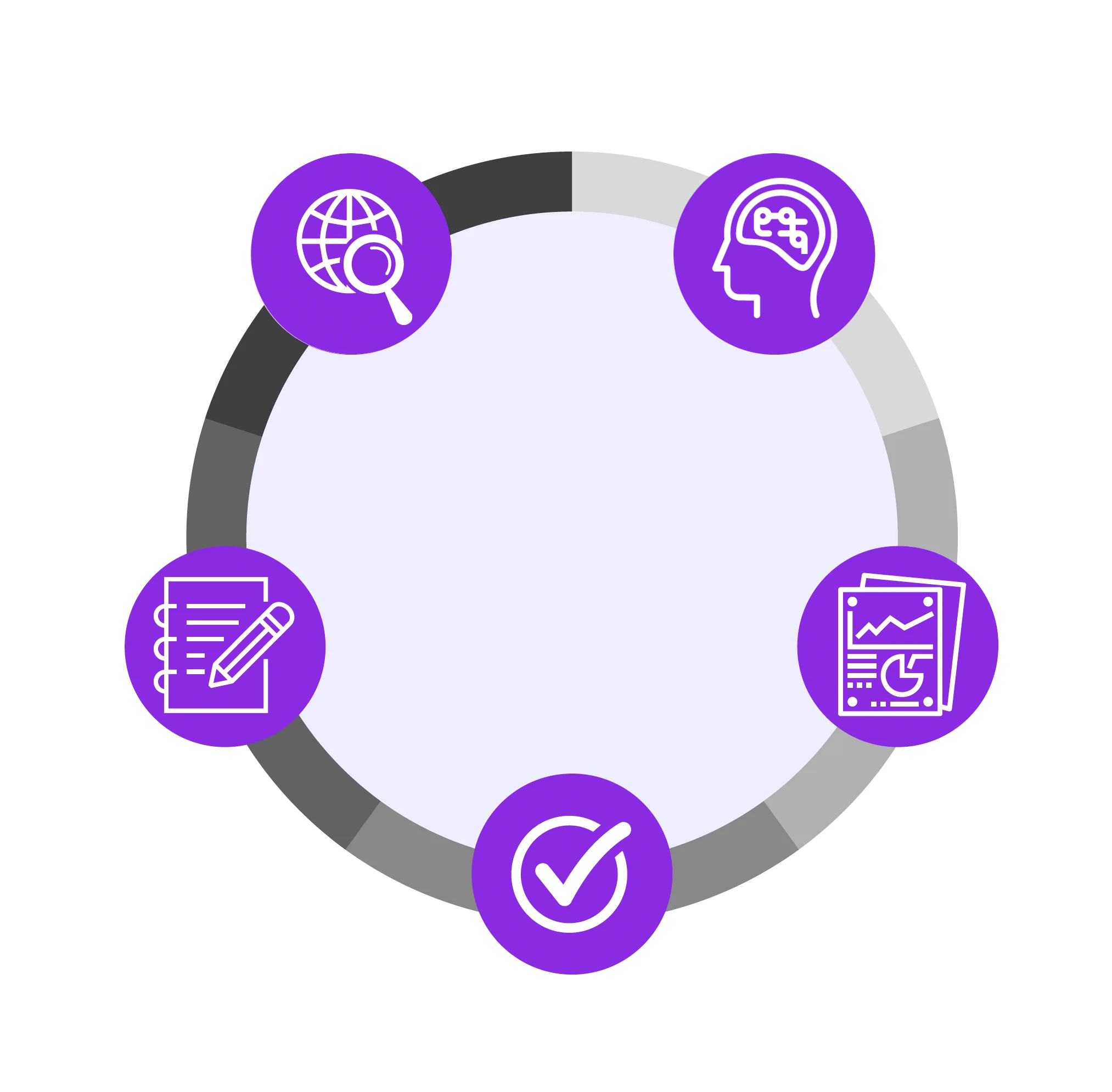
Vulnerability
Management
04. Remediate
Fixes vulnerabilities by
patching or applying other
security controls
02. ASSESS
Scans all identified assets
for vulnerabilities
03. Analyze
Interprets the
vulnerabilities in your
infrastructure context

01. Discover
within your environment

02. Assess
for vulnerabilities

03. Analyze
vulnerabilities in your
infrastructure context

04. Remediate
patching or applying other
security controls

05. Test Remediations
vulnerabilities are fixed

Today’s Security Challenges
The cost of an average data breach rose from $3.86 million to $4.24 million, with lost business representing the largest share of these costs, at $1.59M [1].
HIFENCE Vulnerability Management provides the
comprehensive testing of your environment to keep your
infrastructure and company safe and secure.
Most companies are reactive to cyber threats, paying attention to cybersecurity only after they are breached — and that’s far too late.
By performing a vulnerability scan on your whole infrastructure, you can make sure that you are proactive and are able to identify the cyber threats before any bad actor has a chance to take advantage of them.
It takes an average of 287 days — that’s over 9 months — to detect and contain a breach, with 212 days needed just to identify a breach, and 75 days to contain it [2].
While performing our vulnerability tests, you can also test
your internal security team to see if they can identify, alert
and stop the actions performed by the vulnerability tool.
Two of the most common initial attack vectors in 2022 were
vulnerabilities in 3rd party software and cloud misconfiguration, responsible for 28% of breaches that amounted to an average of loss of $8.69M [3].
But by performing the security pentest, you can make sure
that you are proactive and identify the cyber threats before
any bad actor has a chance to take advantage of it.
How Does HIFENCE Vulnerability Management Help?
With decades of experience, HIFENCE security experts provide advanced vulnerability services that will expose your infrastructure weaknesses. We then make recommendations on how you can fix them to further improve your security posture.
Key Capabilities
Features
What’s included
Custom Scans
scans.
Authenticated Scans
HIFENCE performs both authenticated and unauthenticated scans so you can have a more thorough view on your vulnerability landscape.
Internal and External Scans
HIFENCE performs scans from within or outside your network, which provides you with visibility from all
sides.
Vulnerability Tracking
to be fixed.
Vulnerability Contextualization
Vulnerability Remediation
Integration with 3rd Party Ticketing Systems
HIFENCE can integrate easily with most 3rd party ticketing systems.
Reporting
Industry Compliance
Powered by Teenable
Know It All:
Get the Penetration Testing Datasheet
You’ll learn, in clearly explained detail, how the features and benefits of our Penetration Testing services will help your company be safer and more secure, so you can focus on its success.

What makes us
different
You’ll like this: We’re not like other Cybersecurity providers.
We didn’t set out to have a different way of delivering the best Cybersecurity and Networking services you can have. But we — and our clients — are glad we do.
The difference is simplicity.
You’ll like this: We’re not like other Cybersecurity providers.
We didn’t set out to have a different way of delivering the best Cybersecurity and Networking services you can have. But we — and our clients — are glad we do.
The difference is tossing out
the cookie cutter.
The difference is all that we do is protect all that you do.
The difference is we’ll provide everything you need, and not
one thing you don’t.
Schedule Your
Free Consultation
A HIFENCE expert will conduct a quick overview of your current cybersecurity and networking infrastructure and discuss roadmaps for achieving your desired level of protection, based on your business objectives.
