Protect your company from
cybersecurity risks with the
NIST Cybersecurity Framework (CSF)
Developed by the US National Institute of Standards and Technology (NIST), the NIST Cybersecurity Framework (CSF) provides clear and actionable standards, guidelines and best practices that help organizations improve their information security and cybersecurity risk management.
A key to NIST CSF’s broad utility is its being structured around a framework which enables disparate parties and internal and external stakeholders to abide by a common set of cybersecurity guidelines to assess, prioritize and mitigate cybersecurity risks.
Key Business Benefits
- Strengtens the trust among business partners, clients and stakeholders; a strong cybersecurity posture is particularly important in B2B transactions.
- Business and technical teams can speak the same language. The risk-based approach of NIST CSF is easy to understand and use, allowing all stakeholders to communicate effectively.
- Ensures a better understanding of your current security risks and allows you to address the most critical ones.
- An excellent starting point to build compliance with other standards (ISO 27000, HIPAA, SOX, PCI-DSS, among others), most of them having the same goal: to improve your cybersecurity posture.
- Enables business growth as it creates a valuable selling point for suppliers and vendors. Most partners are vested in your cybersecurity practices, as they want to be sure they are not exposed to supply chain risk.
- Creates a framework that enables different parties to abide by a common set of cybersecurity guidelines to assess, prioritize and mitigate risks from cyberattacks.
- Provides an opportunity for organizations to establish roadmaps for their journey to managing cybersecurity risks more effectively.
NIST CSF Requirements
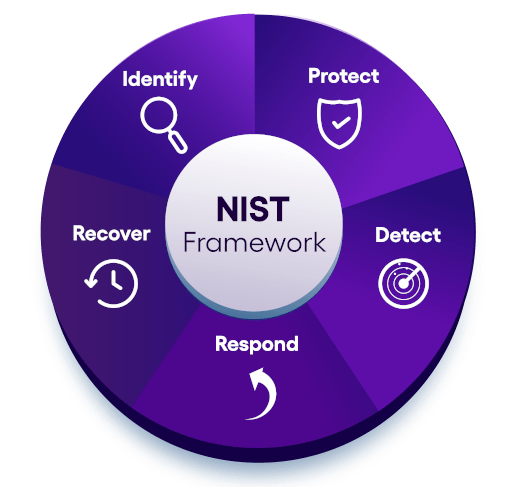
NIST CSF guidelines are divided into five specific Functions: Identify, Protect, Detect, Respond, and Recover, with each Function presenting from three to six Categories of specific actions or elements. HIFENCE can help you comply with NIST CSF Functions and Categories to enhance your company’s cyber resilience and protect your critical infrastructure.
IDENTIFY
Assess which of your business assets are at risk of cyberattacks
While the identify function covers asset management, it also goes further to include the identification of the business environment, governance, and a risk management strategy that includes risk assessment.
The Identify function is broken up in the following categories:
Asset Management
Determining the business environment
Governance
The policies, procedures, and processes to manage and monitor the organization’s regulatory, legal, risk, environmental, and operational requirements are understood.
Risk Assessment
Risk Management Strategy
Supply Chain Risk Management
Asset Management
Identifies the entire flow of traffic among assets, and then shows which external-facing assets are most at risk.
HIFENCE provides active scanning, passive monitoring and CMDB integrations to help you identify all of your assets, both known and previously unknown.
HIFENCE Security Services
How we can help
Business Environment
Governance
Supply Chain Risk Management
Risk Management Strategy
We deliver a detailed roadmap showing how HIFENCE Security Architecture enables you to identify the business environment, improve your governance and risk management and manage your supply chain risk.
Risk Assessment
We will first determine if vulnerabilities already present in your posture are prime targets for a cyberattack. We then elevate the asset risk to a high-risk threshold.
HIFENCE Security Services
How we can help
Asset Management
Identifies the entire flow of traffic among assets, and then shows which external-facing assets are most at risk.
HIFENCE provides active scanning, passive monitoring and CMDB integrations to help you identify all of your assets, both known and previously unknown.
Business Environment
Governance
Supply Chain Risk Management
Risk Management Strategy
We deliver a detailed roadmap showing how HIFENCE Security Architecture enables you to identify the business environment, improve your governance and risk management and manage your supply chain risk.
Risk Assessment
We will first determine if vulnerabilities already present in your posture are prime targets for a cyberattack. We then elevate the asset risk to a high-risk threshold.
PROTECT
Implement safeguards to keep your assets secure
The Protect function demands the development and implementation of relevant safeguards to make sure that critical infrastructure services are protected. It is divided into 6 categories:
Identity Management, Authentication and Access Control
Awareness and Training
Data Security
Information Protection Processes and Procedures
Maintenance
Protective Technology
HIFENCE Security Services
How we can help
HIFENCE Security Services
How we can help
Identity management, Authentication and Access Control
The firewall hardens your most basic and first level of defense to protect your environment, and it provides authentication, network segmentation and access control.
Identity management, Authentication and Access Control
The firewall hardens your most basic and first level of defense to protect your environment, and it provides authentication, network segmentation and access control.
Awareness and Training
Data Security
We develop a holistic Cybersecurity strategy to assure that your users have proper awareness and training and that your data is securely stored, to maintain its confidentiality, availability and integrity.
Awareness and Training
Data Security
Information Protection Processes and Procedures
Maintenance
Critical in helping you prioritize the hierarchy of controls for your assets.
Information Protection Processes and Procedures
Maintenance
Critical in helping you prioritize the hierarchy of controls for your assets.
Protective Technology
Helps to protect your assets from breaches and attacks in your endpoints by providing detection and response services.
Protective Technology
Helps to protect your assets from breaches and attacks in your endpoints by providing detection and response services.
DETECT
Actions to determine if a data breach or a cyber attack has occurred
The Detect function specifies the need to develop and implement a good cybersecurity program to be able to detect any cybersecurity events and incidents.
It is divided into 3 categories:
Anomalies and Events
Security Continuous Monitoring
Detection Processes
HIFENCE Security Services
How we can help
HIFENCE Security Services
How we can help
Anomalies and Events
Helps identify the entire flow of traffic among assets, and enables you to pinpoint the original entry point of that attack.
Anomalies and Events
Helps identify the entire flow of traffic among assets, and enables you to pinpoint the original entry point of that attack.
Security Continuous Monitoring
Helps to protect assets in your entire environment from attacks with detection and response services.
Security Continuous Monitoring
Helps to protect assets in your entire environment from attacks with detection and response services.
Detection Processes
Helps to protect your assets from breaches and attacks in your endpoints by providing detection and response services.
Detection Processes
Helps to protect your assets from breaches and attacks in your endpoints by providing detection and response services.
RESPOND
Taking the most effective actions once a cyberattack is detected
The Respond function supports the ability to contain the impact of a potential cybersecurity incident. You need to develop and implement appropriate activities to take action regarding a detected cybersecurity incident.
It is further divided into 5 categories:
Response Planning
Communications
Analysis
Mitigation
Improvement
HIFENCE Security Services
How we can help
HIFENCE Security Services
How we can help
Response Planning
Communications
We deliver a detailed roadmap showing how HIFENCE ecurity Architecture will strengthen both your response to incidents and your communication to internal and external stakeholders.
Response Planning
Communications
We deliver a detailed roadmap showing how HIFENCE ecurity Architecture will strengthen both your response to incidents and your communication to internal and external stakeholders.
Analysis
Mitigation
Improvement
The firewall correlates with our SOAR platform to rapidly respond by immediately blocking the connection before the attack reaches your internal network.
Detects threats, such as phishing and ransomware attacks, and conducts forensics for a rapid and highly effective response.
Provides detection and response services to help protect your endpoints from breaches and attacks.
Analysis
Mitigation
Improvement
The firewall correlates with our SOAR platform to rapidly respond by immediately blocking the connection before the attack reaches your internal network.
Detects threats, such as phishing and ransomware attacks, and conducts forensics for a rapid and highly effective response.
Provides detection and response services to help protect your endpoints from breaches and attacks.
RECOVER
Actions to maintain or restore services and capabilities affected by a cybersecurity attack
The key aspects of this function are business continuity and continual improvement. After a response to an incident and stabilization of the situation, it is the time to recover and return to business as usual and not to the minimally accepted functionality. With continual improvement, you take actions to prevent the incident from recurring.
The Recover function is further divided into the following categories:
Response Planning
Communications
Analysis
HIFENCE Security Services
How we can help
HIFENCE Security Services
How we can help
Recovery Planning
Improvements
Communication
Restores an affected endpoint back to its previous backup prior to the malware attack, thereby providing recovery.
Recovery Planning
Improvements
Communication
Serves your company’s specific recovery needs and is built around policies, standards and overall capabilities. It can then better serve as a roadmap for recovery planning, improvements and communication.
Limits an attack vector and isolates compromised hosts, enabling the recovery from a data breach.
Restores an affected endpoint back to its previous backup prior to the malware attack, thereby providing recovery.
Schedule your FREE Consultation
We’ll conduct a quick overview of your current cybersecurity posture and present actionable roadmaps to align with the NIST CSF Cybersecurity Framework.